
Products
Data Security On DJI Dock Drone In A Box Software
A guide to data security on DJI Dock software. Learn about the mechanisms in place on solutions such as DJI FlightHub 2, FlytBase, and Drone Harmony to ensure user data is safe when operating the DJI Dock. ... Read More
Find out how DJI Dock software solutions - DJI FlightHub 2, FlytBase, and Drone Harmony - ensure the security of user data;
DJI FlightHub 2 uploads, stores and manages data on cloud servers operated by Amazon Web Services, which are compliant to ISO/IEC 27001 security certifications;
FlytBase has multiple layers of protection, including secure data transfer, encryption, network configuration, and application-level controls, and offers on-premise integration;
Drone Harmony provides options for on-premise server installation or within a private network to ensure critical information remains in operator control;
heliguy™ is a DJI Dock partner, helping organisations integrate the Dock and associated software solutions into their workflows.
Data security is an important consideration when deploying the DJI Dock.

Given the types of organisations using this drone in a box, and the information they will be collecting, it is integral that users have confidence that their data will be safe.
Recognising this, some of the leading software platforms for the DJI Dock have implemented rigorous security measures and protocols.
heliguy™ is a DJI Dock integrator, and in this article, we'll explore the data security architecture of our Dock partner software solutions - DJI FlightHub 2, as well as third-party options FlytBase and Drone Harmony - and illustrate how they ensure the integrity of end-user data.
DJI Dock Data Security On DJI FlightHub 2
FlightHub 2 is DJI's own Dock software. Offering functionality from the cloud, it enables operators to schedule missions, create and edit flight routes, and manage data collected.
As a general message, DJI states that it takes the security of data 'seriously', using 'best-in-class measures to protect the integrity of photos, videos, flight logs, and other user data'.
DJI says that FlightHub 2 is built to maintain integrity across multiple levels of the drone and data-management process, including:
Device connection and maintenance.
Data upload and transmission.
Cloud service storage and operational security.
DJI FlightHub 2's servers are located in Virginia, USA, and uses Amazon Web Services (AWS) as the cloud computing and storage service provider for all regions outside of Mainland China. AWS has ISO/IEC 27001 security certifications - the world's best-known standard for information security management systems.
Alibaba Cloud is used only for customers in Mainland China.
DJI users are not required to store any data with DJI. If they choose to do so, their data is kept in DJI's data centres, equipped with a multi-layer protection mechanism.
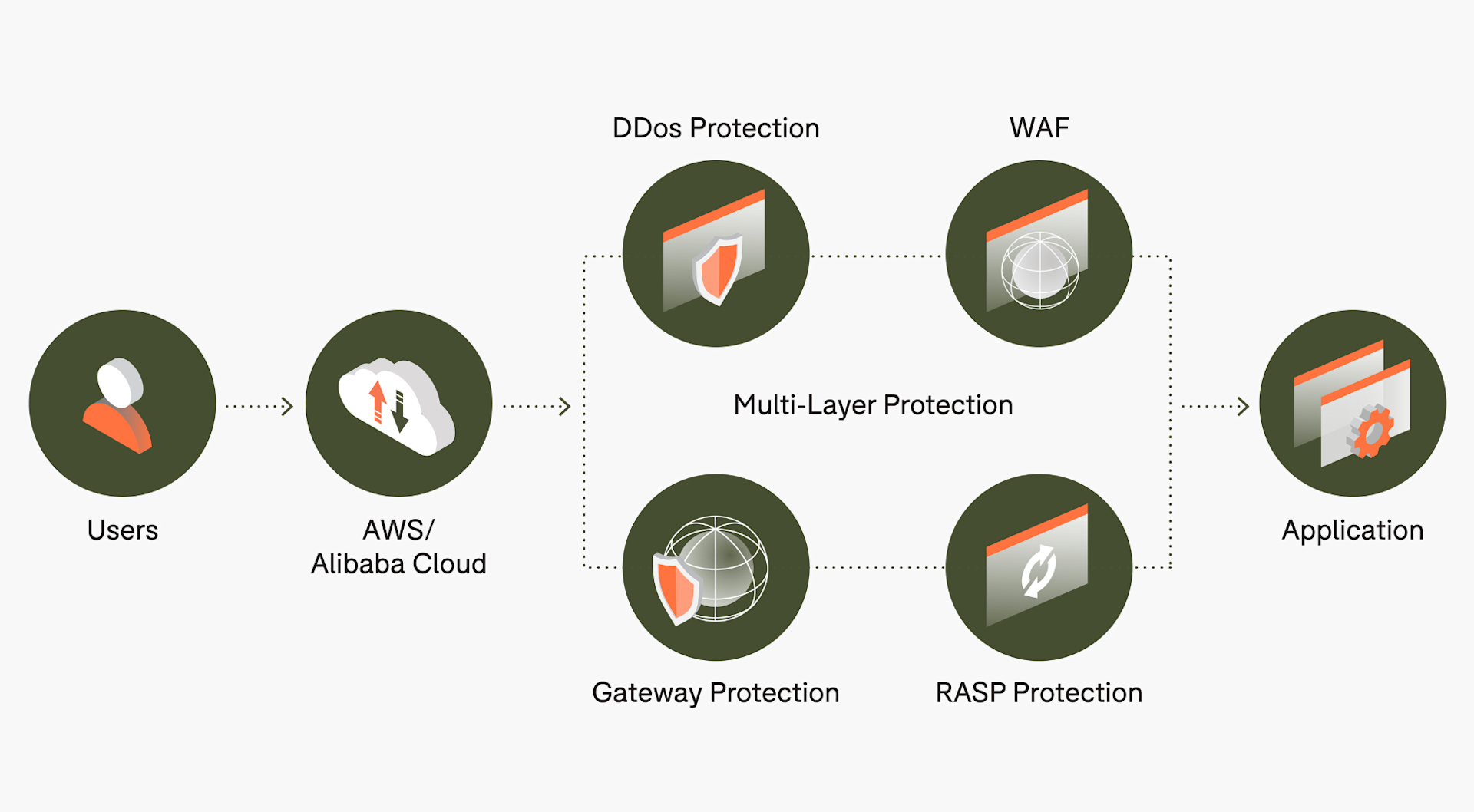
DJI says it will not transmit users' personal information or data across data centres or share any data with third parties. And sensitive information such as email addresses, mobile numbers, and location information is given additional AES-256-CBC encryption - an industry-standard symmetric encryption algorithm.
DJI's security protocols have been scrutinised, examined and confirmed by trusted U.S. cybersecurity firms FTI Consulting, Booz Allen Hamilton, and Kivu Consulting, as well as U.S. federal agencies including the Department of Defense, Department of Interior, Department of Homeland Security and National Oceanic and Atmospheric Administration.
These security protocols and assurances should give operators the confidence to use FlightHub 2, DJI says.
Data Security On FlytBase
FlytBase integrates with DJI Dock to enable automated and repeatable operations.
With multiple layers of protection that includes secure data transfer, encryption, network configuration, and application-level controls, FlytBase is designed with security in mind.
Key factors include:
Public servers located in the USA.
Options for in-country cloud deployments, as well as on-premise cloud deployments.
Compliant with ISO/IEC 27001 and GDPR, and recently recognised as SOC 2 Type II compliant - recognising how FlytBase handles sensitive information.
The FlytBase security architecture looks like this:
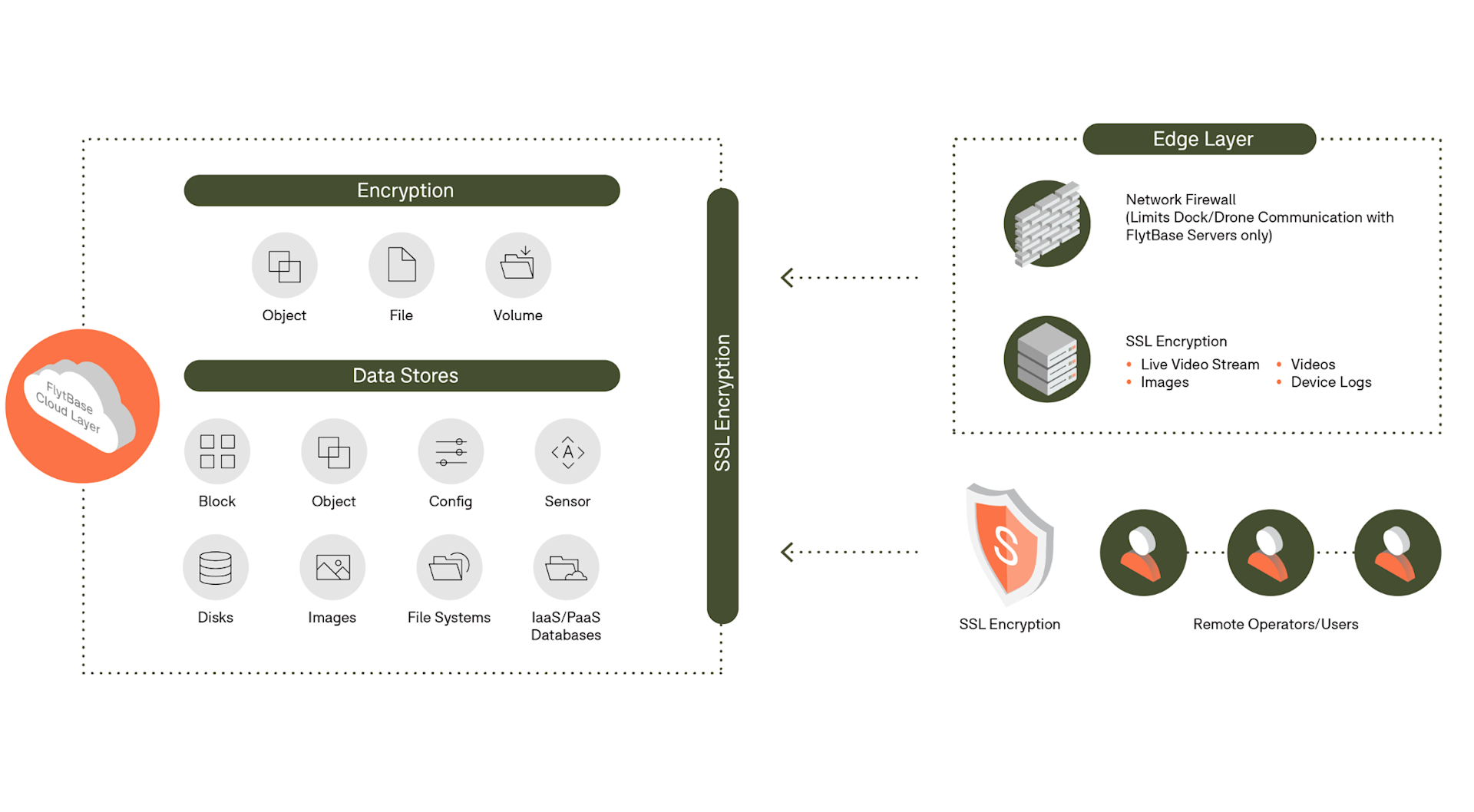
FlytBase uses thorough security protocols to ensure data protection, application security, and user account security.
Security Protocol | Description |
Data Protection | |
Data at rest | All sensitive data, such as passwords, is encrypted at rest and cannot be replicated by anyone. For managing cryptographic keys, FlytBase uses full-disk encryption with the industry-standard AES-256 encryption algorithm and the Azure AD B2C security token service. |
Data in transit | Every network communication with the FlytBase servers and any third-party service provider is encrypted with TLS version 1.2 or higher. Features such as the HSTS (HTTP Strict Transport Security) are also used to ensure the security of data in transit. |
Application Security | |
Vulnerability Scanning & Patching | FlytBase says it follows a stringent vulnerability management process at key stages of our Secure Development Lifecycle (SDLC) to allow early identification of vulnerabilities and resolve them according to predefined timelines based on severity. |
Penetration Testing | FlytBase conducts penetration tests on a regular basis to verify security status and identify potential vulnerabilities. All areas of the FlytBase platform and cloud infrastructure are in-scope for these assessments to maximise the effectiveness. |
User Account Security | |
OAuth 2.0 | FlytBase authenticates and authorises users using the OAuth 2.0 protocol. FlytBase supports the most common OAuth 2.0 scenarios, including web server, client-side, installed, and limited-input device applications. |
Single sign-on (SSO) | FlytBase provides single sign-on authentication with Google and Microsoft, alongside detailed role and team management capabilities within an organisation's profile. Enterprise users have the flexibility to use their own SAML 2.0-compliant solution. |
FlytBase also offers flexible deployment options, including the option to operate on a separately managed AWS environment with physical isolation from the shared infrastructure of the multi-tenant cloud offering, giving an additional layer of security and privacy.
Deployment Option | Description |
Multi-tenant | Seamlessly integrate with your private cloud storage, enjoy consistent, hassle-free maintenance managed by FlytBase, and easily scale your operations. |
Sole-tenant | Enjoy exclusive access on a private instance, enhanced security, compliance with data residency laws and customisation control over server configurations. |
On-Premise Hybrid | Ensure data privacy by hosting drone media on local servers, while maintaining a secure connection to multi/sole tenant servers for command and control. |
Air Gap | Meet compliance with data governance laws and internal IT policies while enhancing latency, management and control, data security, and storage capabilities. |
Speaking at the UK's first DJI Dock demo event, hosted by heliguy™, Nitin Gupta, FlytBase CEO and Founder, said: "Data security is an important concern for our enterprise customers, including large oil and gas companies, utility companies, and public safety departments, so they do not want any of their data going onto servers that they do not trust.
"We offer options for in-country cloud deployments as well as on-premise cloud deployments, so for some customers who are ultra sensitive about data and they want all of the data to reside inside their premise, we offer air-gapped deployments where zero data is being transmitted or shared on the network.
"This means that everything is within a customer's private networks - that way they are 100% guaranteed that no data is going to any server they do not trust, and everything is on their premise or within their country."
Drone Harmony Data Security
Drone Harmony offers situational awareness, planning, and visualisation capabilities for DJI Dock sites, including intuitive 3D flight management.
Based in Switzerland, Drone Harmony says the security of sensitive data is a paramount concern and addresses this by providing options for deployment on a client's server (on-premise) or within a private network to ensure critical information remains in operator control.
Martin Fuchsberger, co-founder and CEO of Drone Harmony, said: "It is important that user data is not going anywhere where the client doesn't want it to be, so we offer tiered solutions.
"The on-site premise solution, where we install it for you in your infrastructure so the data never leaves your premises, is a good solution for someone who is looking for an absolutely secure infrastructure solution.
"We also offer something in between, where clients use our servers or cloud servers from AWS or Azure. This means the servers are in Europe and provides users with some control of where the data will be.
"All of this combined addresses different security needs from our clients."
Drone Harmony is also in the process of securing ISO 27001 certification.
Summary
Data security is a vital component of deploying the DJI Dock.
Or more pertinently, it is crucial that operators feel confident that their sensitive information is safe and secure.
From industry-leading encryption through to on-site server options, DJI Dock software offers a range of features to ensure this.
To discuss data security, the DJI Dock and any of the software solutions covered in this article, contact us. heliguy™ is a DJI Dock partner and can help organisations integrate this drone in a box into their workflows.
